We live in the age of AI hype. Artificial intelligence is here, there, and everywhere – so promising, slightly mysterious, but undeniably guiding humanity toward a brighter future of technological singularity that’s still somewhat incomprehensible and potentially a black hole.
Some readers might detect sarcasm in this statement – but that would be a mistake. Machine learning-driven automation (ML), neural networks, and other AI technologies have already taken over many industries. And there’s more to come in the evolution of Homo sapiens. If you’re interested in diving deeper into this topic, check out the history of the various industrial revolutions: first, second, third, and even fourth.
In line with this trend, cybersecurity was perhaps one of the pioneers in adopting new, smart technologies. And what makes me particularly proud of this process is that our company was one of the first in the industry to successfully implement this bright AI-driven future. How else could we possibly handle nearly half a million new malicious programs emerging every single day as of early 2025? No educational system in the world can produce enough experts to keep up with that. The only solution is to create intelligent systems capable of independently and highly accurately neutralizing cyberattacks. Experts are then left with only the most complex cases – and, of course, the challenging task of inventing and continuously improving these systems.
A few days ago, we celebrated an exciting anniversary. Twenty years ago was born the prototype of our first AI/ML technology for automatic malware analysis and the creation of “detections” – antivirus updates that protect computers, gadgets, and other devices from new attacks.
The technology was given a name that’s rather odd at first glance – Avtodyatel, which translates as Auto-Woodpecker! But there’s a simple explanation for it: within our team, security analysts were affectionately referred to as woodpeckers – tirelessly pecking away at viruses and processing streams of suspicious files. And then we added the “Auto” to “Woodpecker” for the name of the tech designed to do this job automatically (incidentally, I was a woodpecker myself back then).
After digging through our archives, we found not only the birthdate of this first automation baby, but also some fascinating photos of the original plans for its creation. We even recalled its birthplace – the 14th floor of the Radiophysics building near the Planernaya metro station in northwest Moscow where we rented office space at the time. So get comfy, and I’ll tell you a fascinating story. It all started kinda like this…
A quarter of a century ago, malicious programs were much rarer – and, paradoxically, much more advanced – than today’s typical malware, despite being written by pioneering enthusiasts, inventive lone programmers, and cyber pranksters. This made researching them a real pleasure – each new virus taught you something new. Back then, like my fellow woodpeckers, I manually analyzed the stream of malicious programs – what would now be called “malware research”.
By that time, it was already difficult to compile all existing malware into a single reference book as had been done back in 1992. But we still managed the flow, and at the end of each work week, I manually compiled antivirus database updates.
However, over time, malware creation evolved from mere mischief and boundary-pushing into a full-fledged criminal industry. Cybercriminals no longer just wanted to infect as many computers as possible – they sought to profit from it. For example, they harvested email addresses from infected machines and sold them for spam distribution.
Sensing profit, these bad actors triggered exponential growth in malware production. But instead of inventing fundamentally new threats, they started mass-producing slightly modified versions of existing ones. And I realized we couldn’t keep up manually; if we were to continue down this path, we’d drown in an endless flood of cyber-garbage.
Fortunately, technological advancements at the time required much smaller investment and less development time. You could just buy some pizza (pineapple-topped, of course!), gather a few brilliant minds in a meeting room, and spend a couple of hours brainstorming project ideas. And so, on February 22, 2005, I assembled my colleagues to develop plans for automating our malware analyst work.
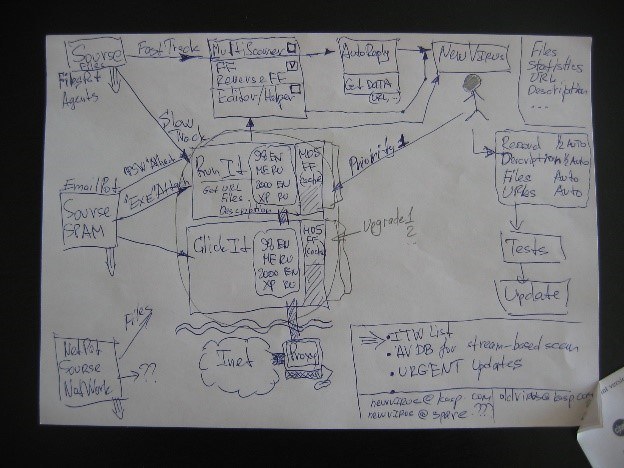
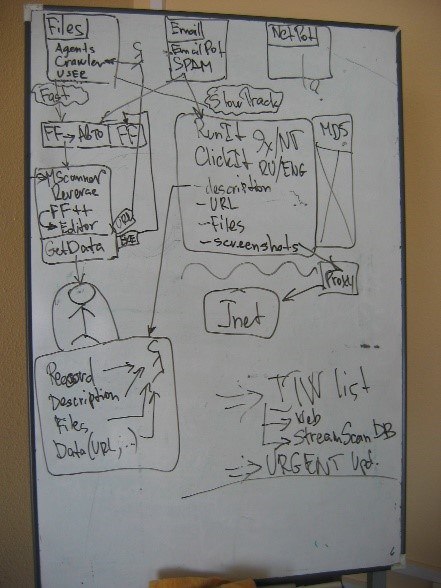
Just take a look at this beauty!
We had some primitive automation tools before, of course. But Auto-Woodpecker was the first system with a fundamentally new level:
- It freed up valuable experts from repetitive tasks, allowing them to focus on more advanced challenges.
- It massively scaled up operational efficiency.
- It helped highlight similar (or related) incidents for further analysis.
In simple terms, the system automatically received new files from agents (“crawlers”) that scanned websites, email traps, and network sensors. These files were then automatically unpacked and executed in a secure environment – an artificial setting designed to observe malware behaviour.
There, the samples were analyzed by automated scanners, classified, and then compiled into antivirus databases.
The key challenge when encountering a new malware sample was determining whether it was a never-before-seen threat, or simply a variation of a known one. This is where the file auto-classifier (marked as “FF” in the diagram above) came into play, utilizing AI/ML principles – now an essential feature in nearly every cybersecurity product (except for fraudulent ones).
It didn’t work perfectly at first, but it quickly improved. We systematically documented all our ideas, detailed how subsystems would interact, how data would be exchanged, and how false positives would be handled. Then we rolled up our sleeves and got to work.
A few months later, the first version of Auto-Woopecker went live.
The results were instant and dramatic. Previously, five of us manually analyzed around 300 malware samples per week – an impressive number at the time. But with Auto-Woodpecker our productivity skyrocketed. And as the technology improved, this skyrocketing just kept on… skyrocketing!
Before long, Auto-Woodpecker was processing the entire incoming stream – leaving only 2-5% of all suspicious files for manual expert review. Today, of course, our tools are far more advanced, and AI-driven technologies play an even bigger role in cybersecurity.
To give you a glimpse of how far we’ve come, here are just a few recent examples:
- Kaspersky MLAD (Machine Learning for Anomaly Detection): A predictive analytics system that detects early signs of equipment failure, process disruptions, cyberattacks, and human errors in industrial telemetry signals – long before they cause real damage.
- Kaspersky MDR (Managed Detection and Response) This service has been using an AI analyst for several years to filter out false positives, reducing the workload on SOC specialists and allowing them to focus on complex threat investigations.
- Kaspersky Threat Lookup: Just last week we integrated a tool for finding contextual information on indicators of compromise using an AI-powered large language model.
The results speak for themselves, and we have even bigger plans ahead!…
Happy 20th Anniversary, Auto-Woodpecker!!
Cin cin!
 AI
AI

 Tips
Tips