
Kaspersky Lab announces comprehensive transparency initiative
Kaspersky Lab announces comprehensive transparency initiative

181 articles

Kaspersky Lab announces comprehensive transparency initiative

What Russian hackers, American spies, the Israeli Intelligence Service, and Kaspersky Lab have to do with each other. What is happening, anyway?

We conducted a global survey of 359 industrial cybersecurity practitioners to learn more about perceptions and realities.

As our research shows, the actual costs of a cybersecurity incident to a financial institution can add up to as much as $926,000.

Banks and financial institutions. require a special approach to IT Security, and that is why we developed a Kaspersky Fraud Prevention Cloud.

How the financial industry reacts to cyberthreats

Shamoon is back with a new version, and this time it is accompanied by another piece of similar malware with far more advanced evasive technologies

True cybersecurity experts must be skilled at reverse engineering. Prior to SAS, Nico Brulez will hold a corresponding training session.

New NSS Labs test utilized new methodology, however it’s results raised some serious questions

Sometimes ATM operators make criminals’ jobs easier by leaving banking machines’ network equipment accessible.

Analysis shows that the attackers are particularly active during the holiday period.

Who is responsible when connected devices go on a crime spree?

Yet another example of an attack against an ATM: This time the cash machine itself is emulated.
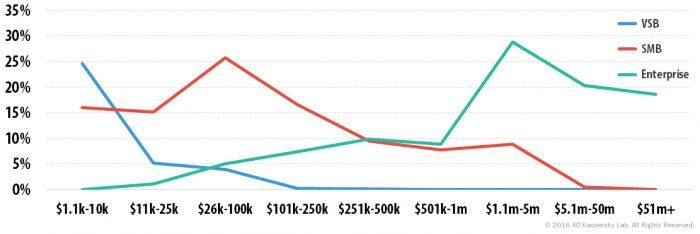
For many SMBs SaaS can provide a cost effective way to take advantage of technology through a cloud-based, subscription model.

To protect critical infrastructure, industrial facilities need a way to share information.

With accessible network cables and a lack of authentication between the ATM and the bank’s infrastructure, ATMs are far too easy to attack.

Our experts made a short video showcasing a proof-of-concept attack by a criminal who has physical access to the ATM’s internals.

We asked more than 3,000 representatives of small and medium-sized companies how they manage to cope with cryptomalware in the constantly changing landscape of cyberthreats.

Mobile banking is easy and convenient, but its adoption rate is still far from ideal.

Kaspersky Lab, the Dutch National Police, Europol, and Intel Security are joining forces to launch a new initiative to battle ransomware worldwide. The initiative is called “No More Ransom.”