
An unusual exploit for Asian banks
The first zero-day exploit for InPage text processor had been used in attacks on Asian banks.

Antivirus Expert, Kaspersky
11 articles

The first zero-day exploit for InPage text processor had been used in attacks on Asian banks.

Cybercriminals are always on the lookout for a new trend to exploit and have developed malware that gives them access to encryption software.

Virtual Desktop Infrastructure is now standard in many organizations. It is as much necessary to set up proper security for virtual systems as it is for the physical infrastructure.

Kaspersky Lab’s security experts released a detailed report on Operation Ghoul – a targeted campaign aimed primarily at businesses in the Middle East and Europe.

Despite the persistent myth of security-by-default, virtual infrastructures need protection every bit as much as physical ones. Almost all existing threats are relevant for virtual machines, too.
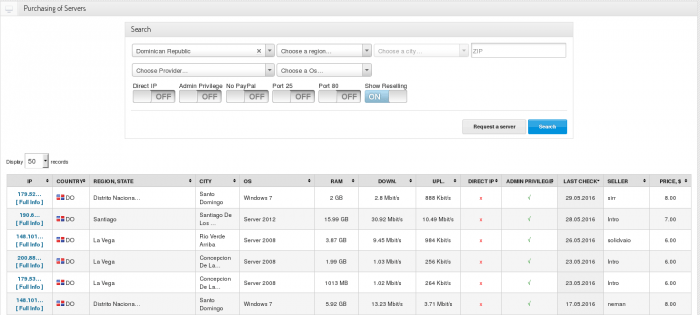
Kaspersky Lab has lately researched an active cybercriminal trading platform xDedic. The main purpose of the xDedic marketplace is to facilitate buying and selling credentials of more than 70,000 hacked servers from all around the world.

The vast majority of targeted attacks begin with simple steps; spear-phishing with malicious attachments or clickable links, or the infection of employees’ favorite websites (water-holing) to penetrate the security perimeter through the vulnerable browsers or other software. Don’t assume that because these methodologies are well-known, they are any less effective.

Do you work with government or military contractors? Or are YOU the contractor? Then be warned: the Sofacy targeted attack actor has scaled up its activities – and may be

These days, the propagation of zero-day exploits occurs almost literally at the speed of light. As soon as such useful exploit makes it to the public, APT authors can begin

Kaspersky Lab experts have investigated a new series of attacks by the Darkhotel cybercriminal group. Here are the details.
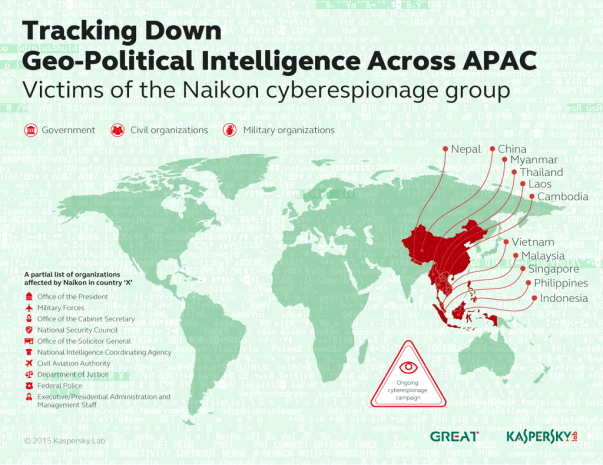
Kaspersky Lab experts have investigated one of the most active APTs (Advanced Persistent Threats) in Asia, operating specifically around the South China Sea area. It was named “Naikon” after the “nokian” User-Agent substring within an attack components’ code.