
The Сyberworld Survival Guide: Control Module
The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

252 articles

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS
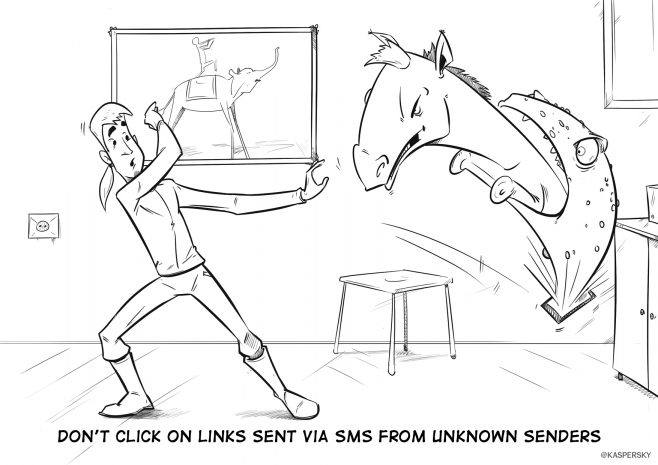
The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS
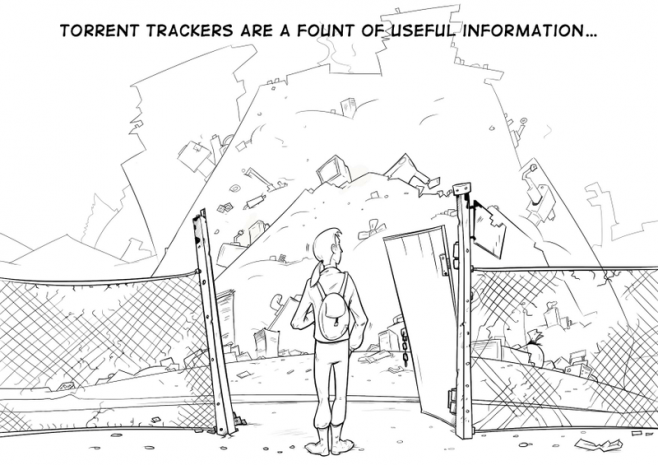
The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS
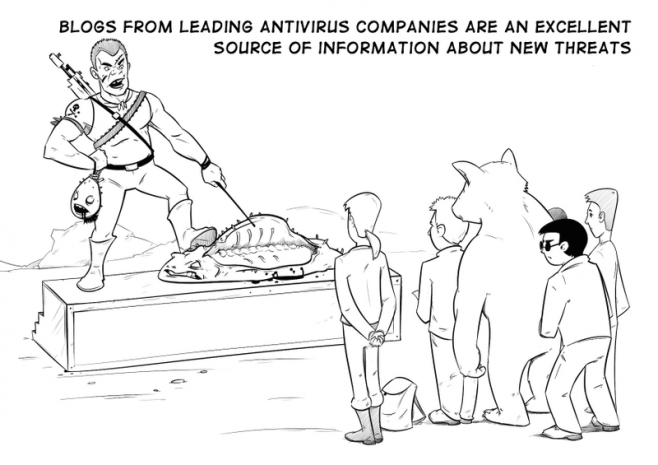
The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The entire series of The Сyberworld Survival Guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

Similar to car crash testing, you’re better off avoiding performing PC security tests yourself. Here’s what the pros have to say for a better, more-trustworthy approach.

Mobile malware is the hottest topic among cybercriminals and the number of malicious mobile apps is rapidly growing. The reason for that is obvious – there are multiple ways to