With each new version of the Android operating system, new features are added to protect users from malware. For example, Android 13 introduced Restricted Settings. In this post, we’ll discuss what this feature involves, what it’s designed to protect against, and how effectively it does its job (spoiler: not very well).
What are Restricted Settings?
How do Restricted Settings operate? Imagine you’re installing an application from a third-party source — that is, downloading an APK file from somewhere and initiating its installation. Let’s suppose this application requires access to certain functions that Google considers particularly dangerous (and for good reason — but more on that later). In this case, the application will ask you to enable the necessary functions for it in your operating system settings.
However, in both Android 13 and 14, this isn’t possible for applications installed by users from APK files. If you go to your smartphone’s settings and try to grant dangerous permissions to such an application, a window titled Restricted Settings will appear. It will say “For your security, this setting is currently unavailable”.
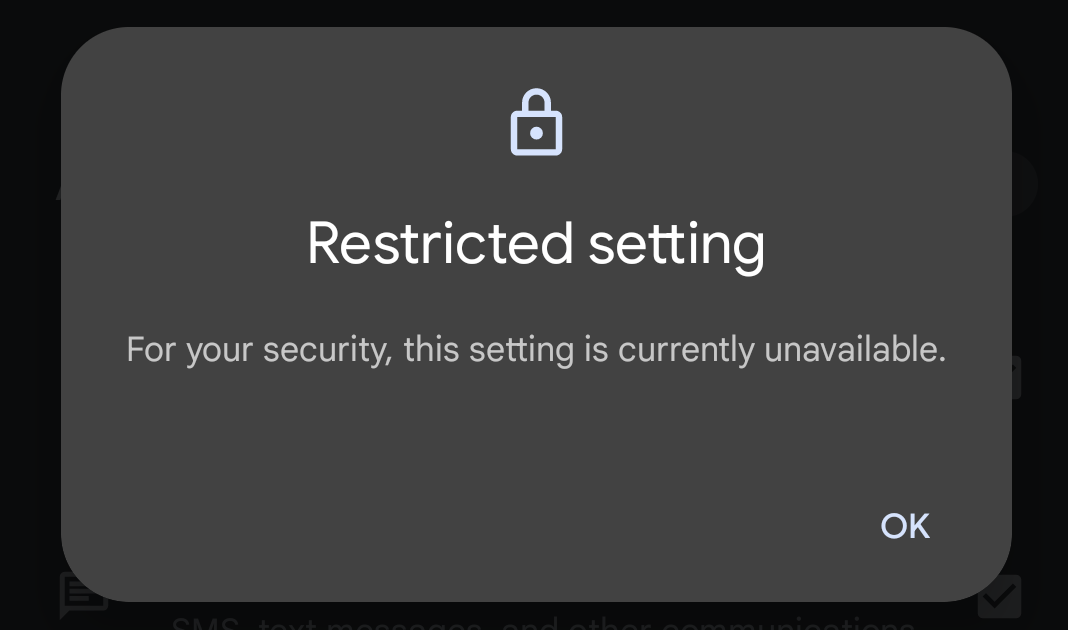
When an application installed from third-party sources requests dangerous permissions, a window pops up with the title Restricted Settings
So, which permissions does Google consider so hazardous that access to them is blocked for any applications not downloaded from the store? Unfortunately, Google isn’t rushing to share this information. We therefore have to figure it out from independent publications for Android developers. At present, two such restrictions are known:
It’s possible that this list will change in future versions of Android. But for now it seems that these are all the permissions that Google has decided to restrict for applications downloaded from unknown sources. Now let’s discuss why this is even necessary.
Why Google considers Accessibility dangerous
We previously talked about Accessibility in a recent post titled the Top-3 most dangerous Android features. In short, Accessibility constitutes a set of Android features designed to assist people with severe visual impairments.
The initial idea was that Accessibility would enable applications to act as mediators between the visual interface of the operating system and individuals unable to use this interface but capable of issuing commands and receiving information through alternative means — typically by voice. Thus, Accessibility serves as a guide dog in the virtual space.
An application using Accessibility can see everything happening on the Android device’s screen, and perform any action on the user’s behalf — pressing buttons, inputting data, changing settings, and more.
This is precisely why the creators of malicious Android applications are so fond of Accessibility. This set of functions enables them to do a great deal of harm: spy on correspondence, snoop on passwords, steal financial information, intercept one-time transaction confirmation codes, and so on. Moreover, Accessibility also allows malware to perform user actions within other applications. For example, it can make a transfer in a banking app and confirm the transaction using the one-time code from a text message.
This is why Google deems the permission to access Accessibility particularly perilous — and rightly so. For apps available on Google Play, their use is subject to careful scrutiny by moderators. As for programs downloaded from unknown sources, Android developers have attempted to completely disable access to this set of functions.
Why Google restricts access to notifications
We’ve covered Accessibility, so now let’s talk about what’s wrong with applications accessing notifications (in Android, this function is called Notification Listener). The danger lies in the fact that notifications may contain a lot of personal information about the user.
For example, with access to all notifications, a malicious app can read almost all of the user’s incoming correspondence. In particular, it can intercept messages containing one-time codes for confirming bank transactions, logging in to various services (such as messengers), changing passwords, and so on.
Here, two serious threats arise. Firstly, an app with access to Notification Listener has a simple and convenient way to monitor the user — very useful for spyware.
Secondly, a malicious app can use the information obtained from notifications to hijack user accounts. And all this without any extra tricks, complex technical gimmicks, or expensive vulnerabilities — just exploiting Android’s built-in capabilities.
It’s not surprising that Google considers access to notifications no less dangerous than access to Accessibility, and attempts to restrict it for programs downloaded from outside the app stores.
How Android malware bypasses Restricted Settings
In both Android 13 and 14, the mechanism to protect against the use of dangerous functions by malicious apps downloaded from unknown sources operates as follows. App stores typically use the so-called session-based installation method. Apps installed using this method are considered safe by the system, no restrictions are placed on them, and users can grant these apps access to Accessibility and Notification Listener.
However, if an app is installed without using the session-based method — which is very likely to happen when a user manually downloads an APK — it’s deemed unsafe, and the Restricted Settings function is enabled for it.
Hence the bypass mechanism: even if a malicious app downloaded from an untrusted source cannot access Accessibility or notifications, it can use the session-based method to install another malicious app! It will be considered safe, and access restrictions won’t be activated.
We’re not talking theory here – this is a real problem: malware developers have already learned to bypass the Restricted Settings mechanism in the latest versions of their creations. Therefore, the restrictions in Android 13 and 14 will only combat malware that’s old — not protect against new malware.
How to disable Restricted Settings when installing an app from third-party sources
Even though it’s not safe, sometimes a user might need to grant access to Accessibility or Notification Listener to an app downloaded from outside the store. We recommend extreme caution in this case, and strongly advise scanning such an application with a reliable antivirus before installing it.
To disable the restrictions:
- Open your smartphone settings
- Go to the Apps section
- Select the app you want to remove access restrictions for
- In the upper right corner, tap on the three dots icon
- Select Allow restricted settings
That’s it! Now, the menu option that lets you grant the app the necessary permissions will become active.
How to protect your Android smartphone
Since you can’t rely on Restricted Settings, you’ll have to use other methods to protect yourself from malware that abuses access to Accessibility or notifications:
- Be wary of any apps requesting access to these features — we’ve discussed above why this is very dangerous
- Try to install applications from official stores. Sometimes malware can still be found in them, but the risk is much lower than the chance of picking up trojans from obscure sites on the internet
- If you really have to install an app from an unreliable source, remember to disable this option immediately after installation
- Scan all applications you install with a reliable mobile antivirus.
- If you’re using the free version of our protection tool, remember to do this manually before launching each new application. In the paid version of Kaspersky for Android, this scan runs automatically.
 Android
Android
