Bright lights, big city: Kaspersky Lab UK relocates to London
Kaspersky Lab today announces the opening of a new flagship European office in central London. Serving as an official ‘hub’ for European employees and customers, the new office will position
 Business News
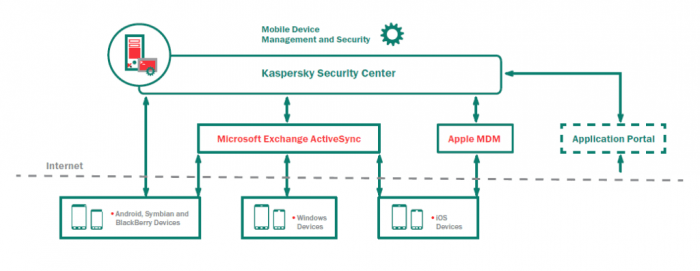
Business News BYOD
BYOD
 Kaspersky Lab
Kaspersky Lab
 cybercriminals
cybercriminals

 Ferrari
Ferrari

 anti virus
anti virus

 kaspersky antivirus
kaspersky antivirus