Information security digest: July 18 – August 18, 2013
Apple Developer Center down for a week It took Apple about a week to restore the functions of the Apple Developer Center following its crash on July 18. After about
3961 articles

Apple Developer Center down for a week It took Apple about a week to restore the functions of the Apple Developer Center following its crash on July 18. After about
Record number of visitors at Gamescom this year Last week, the world’s largest gaming convention, Gamescom, took place in Cologne for the third year running. The many innovations and exclusive

Protecting your home network is as daunting a task as you make it. If your home network consists of a wireless router and a laptop, then it’s pretty easy to
If you use the Internet, then you’re sure to have encountered screen lockers. You may be one of the unlucky people who have encountered that embarrassing moment when an explicit

The number of IT security incidents involving smartphones and tablets is on the rise, and most companies have no plans to limit the use of personal mobile devices for work-related
August has come and gone, you’re home from vacation and you’re ready to settle back into your routine. So make sure you’re prepared for the month ahead by catching yourself

In news that has been making the rounds on various forums since mid-August, analysis conducted by independent IT security research firm MRG Effitas indicates that very few security companies can

Kaspersky Lab today announces the opening of a new flagship European office in central London. Serving as an official ‘hub’ for European employees and customers, the new office will position
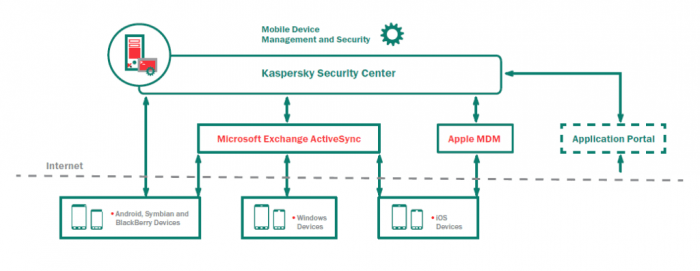
Work does not always require an employee’s presence in the office. In many cases it is acceptable, convenient, and sometimes advantageous for the employee to work remotely from a mobile
MDM systems are often not necessary right away for companies with a small number of mobile workers, whose managers often believe their IT-department can handle it effortlessly. But a reality

Kaspersky Lab just moved into the new HQ building in Moscow. Let’s have a look!

What exactly makes a cybercriminal? Well, without getting into the nitty-gritty of what does and does not constitute a virtual crime, how about we just answer the question: “What makes

A modern man cannot imagine his life without mobile devices like smartphones and tablet computers. A portable minicomputer that provides access to the Internet and offers basic features for processing

You might think that roaring racecars and extreme speeds are forever locked behind a TV screen, but in reality, you encounter Formula 1 every time you sit in your own

If your kids haven’t gone back to school yet, they’re about to. That means school lunches, riding the bus and, of course, homework, are the norms again. And homework, of

Phishing is a dangerous type of Internet fraud that uses fake websites to swipe user logins and passwords to hijack their online accounts to steal money or spread spam and
In the previous ‘Tip Of The Week’ we found out How To Configure A Kaspersky Product To Increase Computer Performance. Today we’d like to revisit this subject and show you

Any movie, be it horror, action or thriller, has a moment that any IT specialist would call comedic, when a demonstration of a mainframe hacking, a virus in action or

According to the cloud-based Kaspersky Security Network, about 200,000 new malware samples emerge every day, compared to 125,000 just a year ago. The price of poor-quality protection against cyber threats

Updated: Current principles for the processing of user data by Kaspersky Lab security solutions and technologies can be found here. According to Kaspersky Lab data, over 200,000 unique malicious samples

It’s no secret to anyone to know that Google keeps every bit of data it collects about each of its users. This data includes, but is not limited to, search