
The State of Mobile Payments and the Rise of Content Driven Commerce
It’s a weird time for mobile payments. Years ago it was thought that by now some parts of the world would be well on their way to if not fully
3961 articles

It’s a weird time for mobile payments. Years ago it was thought that by now some parts of the world would be well on their way to if not fully

Strongly encrypted communications are secure and private communications (as long as there is no monkey-business going on in the way the encryption is implemented into communications software or protocols). Therefore,

DDoS attack without head… A powerful and very unusual DDoS attack was discovered in mid-October. The attack was unusual in that it employed a version of the Phantom JS headless

There is an all-too common misconception that in order to become infected with web-propagated malware, you must visit sketchy parts of the Internet’s underbelly or a website within that broad

It’s no wonder that every major figure in show business is not simply an artist, but is an entire business infrastructure. This type of infrastructure is comprised of marketing, sales

If you’re a registered Adobe client, change your passwords now. They have been stolen and published on the Internet, someone even made a crossword puzzle out of them. This is

Do you like our products for home use, but want to ensure the same high level of protection for the computers in your home office or small business? If your

A few days ago Microsoft released a bulletin that described a newly discovered vulnerability (CVE-2013-3906) in several flagship products of the company and reported some detected exploits for it. Attackers

Sending off emails laden with malicious attachments is one of the most effective and widely relied upon methods for disseminating malware and infecting user-machines. It’s tried and it’s true.

As the recent NSA leaks have revealed, our digital lives make it very difficult to maintain anonymity and protect our privacy — especially since we tend to make it especially

Nowadays, we talk a lot about malware that invades our daily activities. Some are more dangerous than others — whether they target private users or companies. Organizations are also threatened
If you haven’t paid for an online transaction in bitcoins yet, chances are you probably will before long. The digital currency that was invented in 2008 has been widely adopted
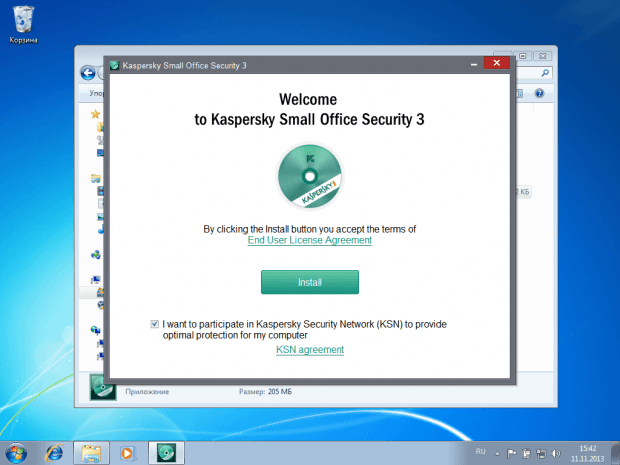
The third version of our small business IT protection kit, Kaspersky Small Office Security, has been released. Let’s take a closer look at what’s available in the new solution. This

When it comes to the dangers of oversharing information through social media, Twitter and Facebook come to most people’s minds. And while we’ve written about the dangers of exposing your

Everyone urges you to invent unique and complicated passwords for each service you use. However, complicated passwords are difficult to memorize, which can lead to a serious problem, especially if
Have you ever performed ritual dances calling to the gods to make your battery last five more minutes? We understand your concern and would like to offer an option that

The newly released Android 4.4 features a tasty new codename (KitKat), some design improvements, revamped Contacts and Hangouts apps, and, of course, several security-related changes. So, how much more secure
On September 30th, a video message appeared on the site of one of the groups of the so-called anonymous hacktivists, in which they talked about planned network attacks at several

While folks in Europe and Russia prepare for the winter and complain about current weather conditions, one brave Russian girl, Olga Rumyantseva, just climbed one more volcano. Olga has undertaken

Ransomware in general is not exactly the nastiest malware out there, but a new variant – called CryptoLocker – is particularly worrisome because it actually does what most ransomware merely