Tip Of The Week: How To Block Games By Age Rating?
In everyday life we encounter a lot of negative things, such as violence, aggression, and brutality. It is often impossible to protect children from such information in the real world,
3951 articles

In everyday life we encounter a lot of negative things, such as violence, aggression, and brutality. It is often impossible to protect children from such information in the real world,

We’re officially into the month of December, which means another month of posts has passed. If you missed anything from November, not to worry, we’ve rounded up some highlights to

In-app purchases are the Holy Grail of revenue for app producers, especially those who make free gaming apps. The hook is that you love the game so much once you

Kaspersky Lab’s Brian Donohue rounds up the latest security news from the month of November 2013. Download podcast for offline listening

The worldwide spread of corporate initiatives like IT Consumerization and Bring Your Own Device makes it necessary to build a return on investment (ROI) model in these promising areas. The

In the U.S. many organizations offer the day after Thanksgiving, which falls on a Thursday, to their workers as a holiday. Brick and mortar American retailers have capitalized on this
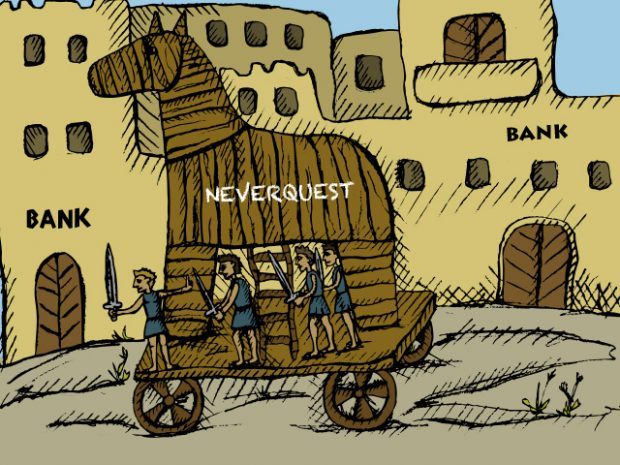
Neverquest is a new banking trojan that spreads itself via social media, email and file transfer protocols. It possesses the capacity to recognize hundreds of online banking and other financial

Times are tough and budgets are tight so when it comes to holiday shopping, everyone’s looking for a deal. However, if your quest for the ultimate savings threatens your safety,

For many Americans, November invokes images of turkey, pie and time spent with family, but for a great deal of others this time of year also brings up something very
You have always had Kaspersky Anti-Virus installed on your computer and have been satisfied with the basic protection you’ve received against common threats. You have started to use Internet banking
The bill for your company’s Internet access just made you grunt in annoyance. And you know exactly who to thank for it. The offender has repeatedly been addressed, but either

It’s a weird time for mobile payments. Years ago it was thought that by now some parts of the world would be well on their way to if not fully

Strongly encrypted communications are secure and private communications (as long as there is no monkey-business going on in the way the encryption is implemented into communications software or protocols). Therefore,

DDoS attack without head… A powerful and very unusual DDoS attack was discovered in mid-October. The attack was unusual in that it employed a version of the Phantom JS headless

There is an all-too common misconception that in order to become infected with web-propagated malware, you must visit sketchy parts of the Internet’s underbelly or a website within that broad

It’s no wonder that every major figure in show business is not simply an artist, but is an entire business infrastructure. This type of infrastructure is comprised of marketing, sales

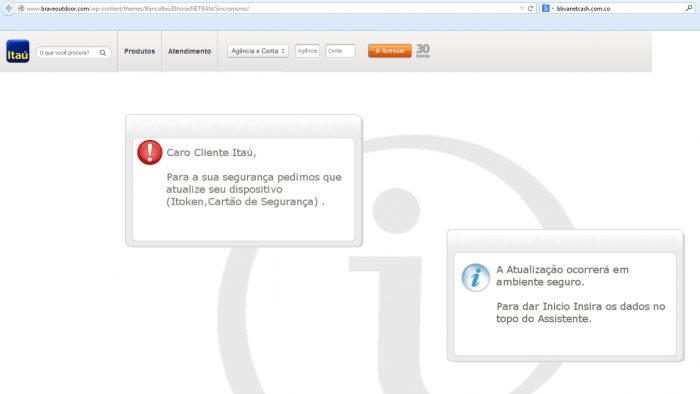
If you’re a registered Adobe client, change your passwords now. They have been stolen and published on the Internet, someone even made a crossword puzzle out of them. This is

Do you like our products for home use, but want to ensure the same high level of protection for the computers in your home office or small business? If your

A few days ago Microsoft released a bulletin that described a newly discovered vulnerability (CVE-2013-3906) in several flagship products of the company and reported some detected exploits for it. Attackers

Sending off emails laden with malicious attachments is one of the most effective and widely relied upon methods for disseminating malware and infecting user-machines. It’s tried and it’s true.