INTERPOL Global Complex for Innovation – Welcome to the future of cybercrime fighting
A huge state-of-art building on 18 Napier Road in Singapore is nestled among the green created by local flora and tropical climate, almost like a spaceship. As written on the
 Cybersecurity
Cybersecurity
 business security
business security
 Cryptowall
Cryptowall
 awards
awards


 #tips
#tips
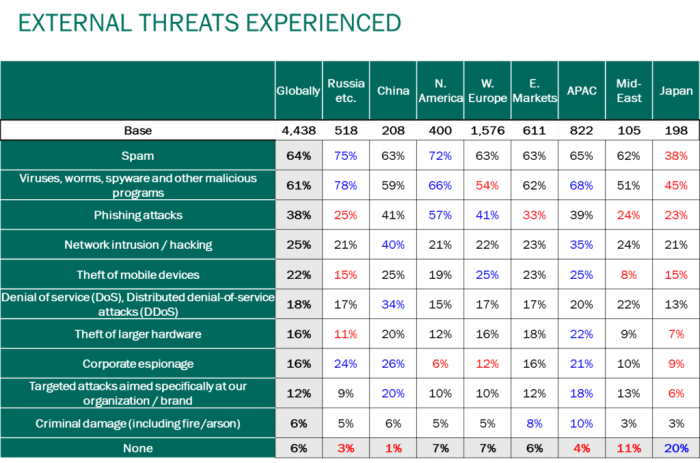
 antispam
antispam #EnterpriseSec
#EnterpriseSec