Misadventures with Hola service, or A lot of strings attached
The primary issue here is the real cost of free offers. Hola’s stance is almost honest: You want free services? You have something that is of use to us – your idle or not-so-idle resources. If you don’t want them to be used by us, there is a paid tier for you.
 free
free
 apple
apple
 #tips
#tips

 books
books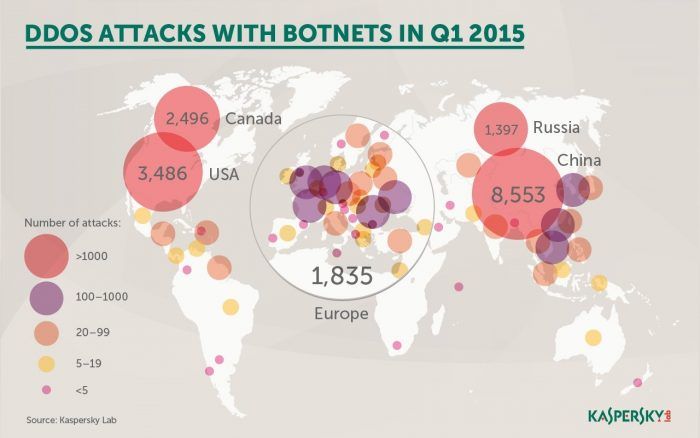
 ddos
ddos




 cyberespionage
cyberespionage





 3D
3D