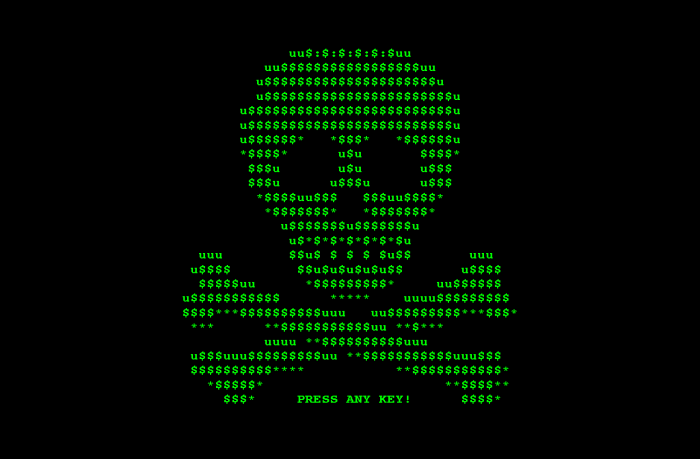
Mischa: a friend for Petya and yet more ransomware for the rest of the world
The Petya ransomware installer now includes another ransomware called Mischa that complements it.
3885 articles

The Petya ransomware installer now includes another ransomware called Mischa that complements it.

Criminals behind the ATM Infector campaign are turning ATMs into invisible skimmers.

Suddenly in an instant I became an outsider in the system. While I was being ‘fixed’, I had an opportunity to think about it and now I can sharee my thoughts with you.

The late April was especially “rich” with news related to bugs, attacks and Android-targeting malware.
An update to RannohDecryptor now allows to beat a newer version of CryptXXX too.

Just took your new iPad out of the box? Here we explain how to make it more secure and easy to use

While many got a good laugh about CryptXXX evolving to beat out tool, ransomware is no laughing matter. Introducing V2 of our tool.


Gartner’s Magic Quadrant is a tool that helps to choose which vendor fits organizations best for a particular business purpose. It is designed for CIO’s, decision makers, and IT-security specialists of the businesses.
Your smartphone knows everything about you: whom you call and what messages you send, which websites you visit and what photos you take, including even when and where you do it. This data may be used against you.

A new APT group is seen to have been exploiting hotpatching, a now-deprecated feature in Windows operating systems, to carry out their attacks.

Do you know how many companies are actually tracking you when you visit a single website? The answer may surprise you.

Discussing what kind of Internet Chinese, North Korean and Indian users have now and what we all might have one day

A 10-year old from Finland successfully discovered and reported an Instagram flaw, and was handsomely rewarded by Facebook.

Locky and Petya ransomware strains took the world by storm when they shouldn’t be successful at all.

Apple iPhone users tend to think their device is absolutely secure. We will take you through several types of attacks which usually target Apple’s smartphones.

Securelist has released a new report on DDoS attacks in the first quarter of 2016.

Reasons why you should pony up the money for your own Wi-Fi and stop stealing it from your neighbors.

Instead of writing their own malicious tools, criminals are increasingly using the off-the-shelf malware, and more and more often – totally legitimate software.

Kaspersky Lab’s GReAT expert Ryan Naraine offers tips to avoid falling victim to ransomware.

We’ve seen drones armed with chainsaws and guns. More alarming though is how easily they can be hacked.