As the total number of vulnerabilities in 2024 continued to climb compared to the previous year, Kaspersky experts warn of cybercriminals increasingly using methods to escalate privileges and exploit weaknesses in digital systems. There is a persistent trend in attacks targeting operating systems, including Linux, which are overshadowing other software categories as prime targets.
Kaspersky data shows that in 2024 operating systems emerged as the most prominent software category for publicly available exploits targeting vulnerabilities (accounting for 57.5%), followed by web browsers (5.4%) and MS Office applications (2.7%).
The number of Linux users encountering exploits rose in 2024 compared to 2023. Specifically, in Q4 2024, the share of such users was 1.5 times higher than in the same period of 2023.
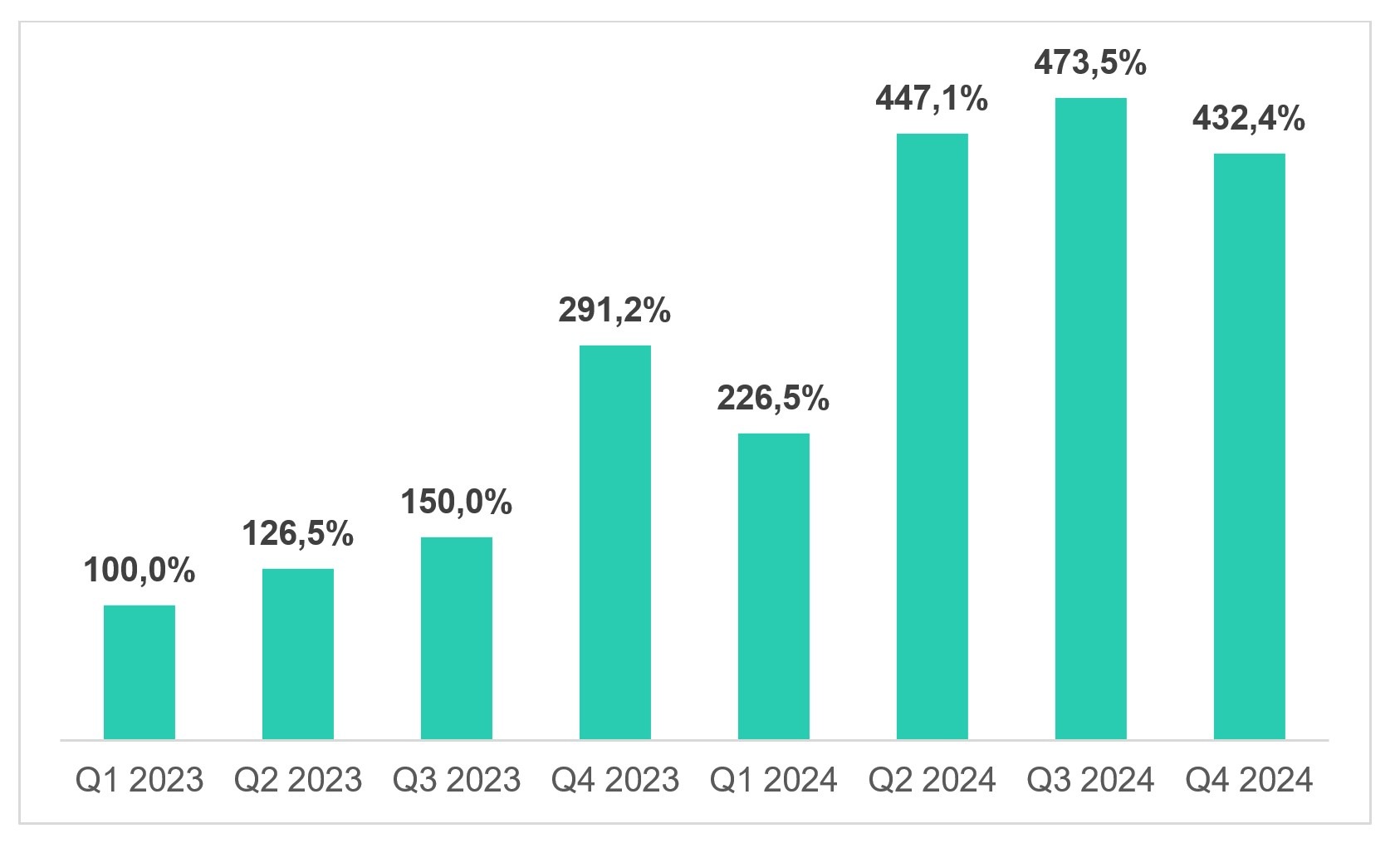
Share of Linux users protected by Kaspersky solutions who faced vulnerability exploits in 2023-2024. Q1 2023 figures are 100%.
Vulnerabilities used in Advanced Persistent Threat (APT) attacks
The list of vulnerabilities commonly exploited in APT attacks highlights shifts in the software targeted by cybercriminals. In 2024, MS Office applications returned to the top ten most exploited software types, reversing a decline from the previous year. For the first time, vulnerabilities in PAN-OS also appeared on the list. Remote access systems and enterprise data processing solutions once again featured among the vulnerable applications. This data underscores a critical issue: the failure to promptly install patches for identified vulnerabilities, which attackers are quick to exploit.
“Looking at 2024, we see several defining trends: a marked increase in the total number of registered vulnerabilities, a reduction in proof-of-concept exploits, and a steady share of vulnerabilities deemed critical by developers. These developments reflect the evolving sophistication of cyber threats and the urgent need for proactive defenses to stay ahead of attackers,” says Alexander Kolesnikov, a security expert at Kaspersky.
According to MITRE ATT&C, while the number of critical vulnerabilities in 2024 remained consistent with 2023 levels, the overall number of registered CVEs (Common Vulnerabilities and Exposures) surged by 20% from 2023 to 2024, rising from 25,011 to 29,976.
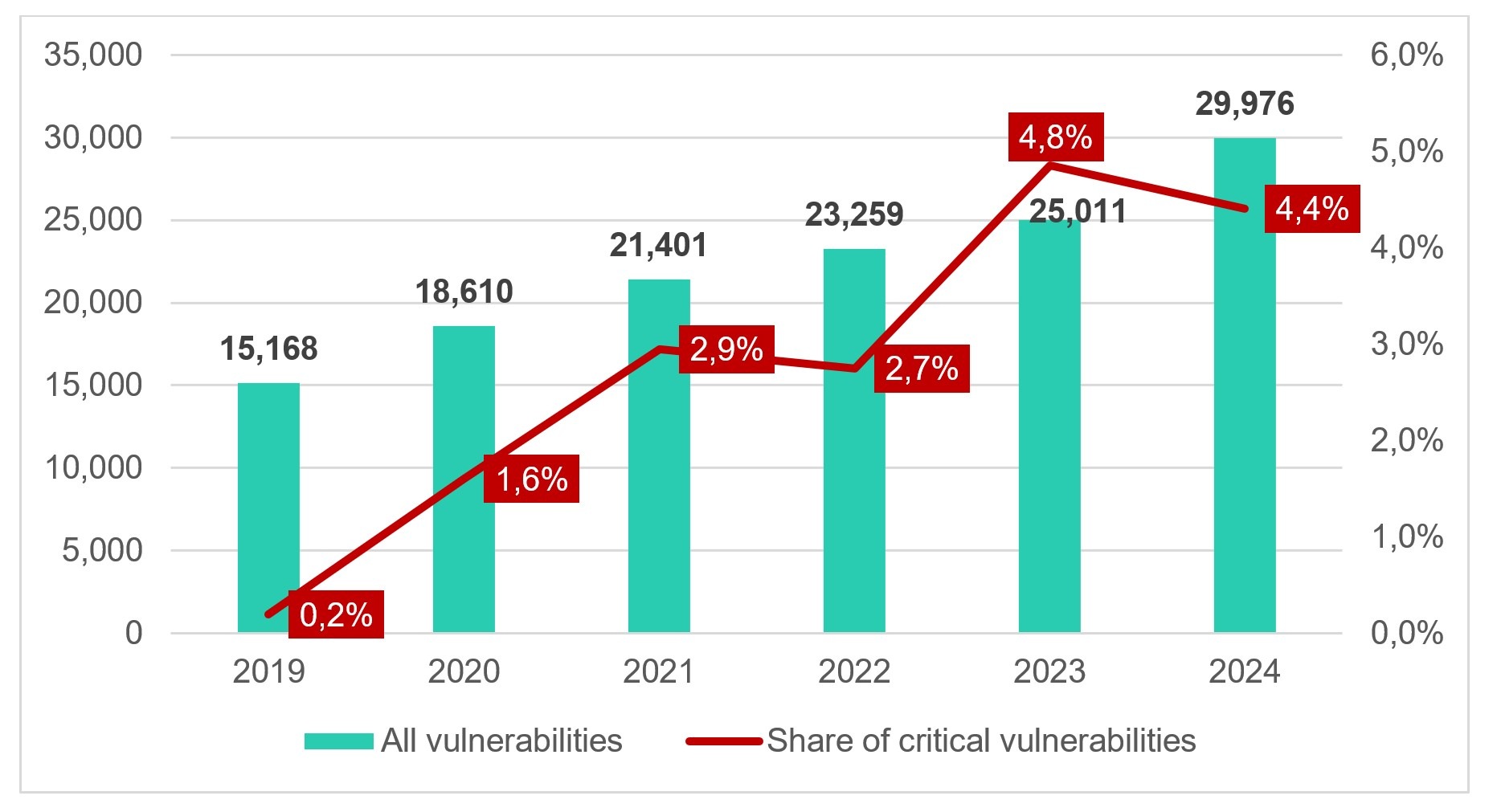
New CVEs with the share of critical vulnerabilities, 2019-2024. Source: cve.mitre.org
To stay secure in this shifting threat landscape, Kaspersky advises organisations to:
- Investigate vulnerability exploits exclusively within secure virtual environments.
- Ensure 24/7 monitoring of infrastructure, with a focus on perimeter defenses.
- Maintain a robust patch management process by promptly installing security updates. To set up and automate this, you can use Vulnerability Assessment and Patch Management and Kaspersky Vulnerability Data Feed.
- Deploy reliable solutions, such as Kaspersky Next, to detect and block malicious software on corporate devices, alongside comprehensive tools that include incident response scenarios, employee training programs, and an up-to-date cyberthreat database.
Read more on vulnerabilities and exploits in the Exploits and Vulnerabilities in Q4 2024 report on Securelist.




